New LACNIC Research Initiative Identifies Open DNS Servers in the Region
26/04/2018
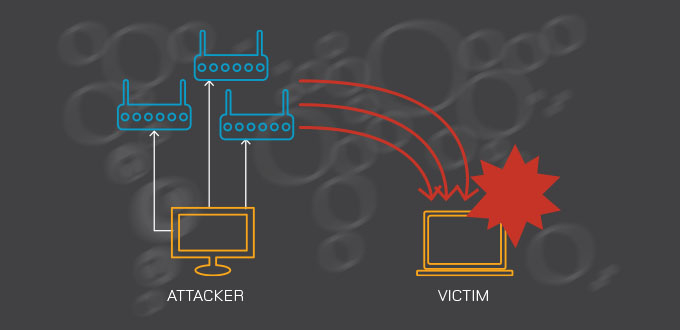
A research project by LACNIC WARP and LACNIC’s R&D department has detected that more than 7% of IPv6 DNS servers in Latin America and the Caribbean are open and therefore vulnerable to attacks.
LACNIC based this analysis on reverse root DNS server D, which translates IP addresses into domain names. Preliminary findings identified that 7.18% of the servers are open and respond when they receive recursive queries, which means that they are vulnerable to being used as amplification DDoS attack vectors, as a small query message allows obtaining a much larger response.
“(7.18%) is a number to which we must pay attention. Our goal is to reduce the number of Open Resolvers detected,” said Alejandro Acosta, R&D Coordinator at LACNIC and one of the persons responsible for the research conducted together with Graciela Martínez, LACNIC WARP Coordinator, and Darío Gómez, Security Analyst at LACNIC.
This work also allowed identifying the organizations operating these open servers, so the next steps will be to develop recommendations, support these organizations so they can fix their configurations, and thus help strengthen Internet security in the region.
The problem of IPv6 DNS Open Resolvers “worries us, as LACNIC WARP has received multiple reports of incidents related to this vulnerability,” Acosta added.
For this reason, together with the R&D department, LACNIC WARP has been working on this project since last December, seeking to understand the current status in the LAC region, identifying open resolvers, and proactively alerting and recommending possible way to correct the configuration of this service. https://labs.lacnic.net/Identificando-servidores-DNS-IPv6-Open-Resolvers/
Once it was implemented, the project managed to detect the open servers in the region. “Ninety-nine percent of the world’s DNS servers should be closed. Reality, however, says otherwise,” observed Acosta.
Preliminary findings highlight that 33,514 records of queries to the reverse root server “D” managed by LACNIC were observed. After analyzing the initial data, researchers found that APNIC is the region most affected by open resolver servers. This region is followed by ARIN and LACNIC, while in RIPE NCC – the region where the largest amount of information was obtained – the number of incorrectly configured servers is almost negligible.
The results of this project will undoubtedly help to strengthen Internet security and stability in our region.
This is the first study on open servers on IPv6 to be conducted in the region. The results will be presented on Thursday 3 May at the LACNIC Technical Forum to be held at LACNIC 29 starting at 15:40 UTC. The presentation will be streamed live.